Analysis of the Learnyst DRM scheme (Part 1)
Disclaimer: The research included in this post is solely intended for educational purposes and does not in any way condone, promote or incite piracy. The consumption of this information shall be carried out at your own risk and the author cannot be held responsible for any damages caused, if any.
Learnyst is a content-serving service catering to small to medium-sized educational creators to help protect their courses from unauthorised sharing and piracy.
The popularity of Learnyst seems to have increased after a period of rampant course piracy by actors who seem to resell such courses at low prices, thereby directly harming the sales of said content providers.
In addition to being a framework provider for educators, Learnyst has a homegrown DRM scheme built on top of their existing Google Widevine / Apple Fairplay framework.
To my knowledge, only 3 versions of Learnyst DRM exist, namely v2, v4 and v6 (only seen being used on web browsers).
Presumably, the difficulty for each one of them increases with the incrementing version number.
This post focuses on the analysis of the v2 version only (later versions might be covered in the future posts).
Discourse - Brief explanation of DRM
Digital Rights Management (DRM) is a technique to prevent unauthorised misuse and copyright infringement of media and software. In the case of media, raw files are “encrypted” by conventional encryption algorithms (such as AES), and the decryption key is kept secure during the transfer flow of the key from the server to the client (in this case, the device playing the media) under secured enveloped structures with complex key derivation algorithms. Playback is either carried out in a hardware-secured enclave such as Qualcomm Trustzone and the Apple Secure Enclave to prevent the interception of decrypted frames, or under a heavily obfuscated userland library if hardware support is not available.
Google Widevine, Microsoft Playready and Apple’s Fairplay Streaming are the examples of media DRM schemes which have sophisticated implementations for both hardware and software protections.
The curious case of Learnyst
Learnyst has devised an even stricter protection scheme to protect their customers’ content. They have developed a custom “DRM” scheme of their own which wraps around the Widevine license messages and encrypts them to make an attack on the same even more difficult than it already is.
Why they have implemented this, beside Widevine already being secure enough, is unknown. Although, it can be speculated that due to the recent public exploits that target Widevine L3 might have rendered it not as effective as it used to be, calling for a revised/improved scheme.
The technicals of Learnyst DRM
There are two ways to implement any sort of DRM.
Protection in a web-app
Protection in a native android application
For (1), Learnyst seems to have implemented a WASM-JS approach to implement their DRM. For (2), a native library has been embedded inside an application protected by Learnyst. This post focuses on the (2)nd way.
I have not been able to analyse the implementation on Apple devices due to the lack of an iOS device.
Obtaining the native library
To obtain the embedded library of Learnyst, one has to obtain and decompress the APK of a Learnyst-supported app. There are many such examples, consisting of mostly educational institutions. However, Learnyst itself offers an app named Learnyst University which offers a couple of free sample courses and are protected by Learnyst DRM!
This seemed to be a good start, but alas, the app actually appears to be broken and neither plays any video, nor is any license request sent to the DRM servers. This approach seems to be a dead end, though the website for the same appears to be functional.
In spite of this, it is wise to isolate the Learnyst Native library responsible for handling all the DRM operations.
To confirm that the DRM operations are handled at the native and not the java layer, the APK was unzipped and baksmali’d with apktool.
It was observed that com.learnyst.lstdrmv2 has very clear references to the native library named lstsec.
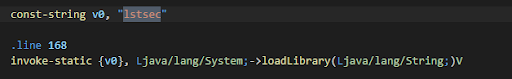
And indeed, it was found that a library named liblstsec.so exists in the APK. Let’s look at it now.
Analysing the native library
Loading the library up in IDA and taking a quick look at the function table reveals the JNI functions, and also indicates an interesting string which probably refers to the Version 2 of Learnyst DRM.
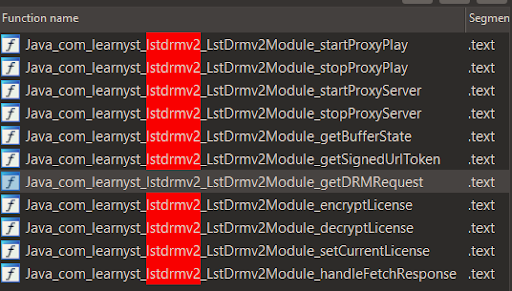
While analysing the JNI functions, some interesting secret keys are uncovered, but they are not important for now and will be documented later.