pee-praghna
Context

It must be said that at this point, India has more coaching institutes than the number of cultures, languages and religions it houses. And naturally, more coaching institutes means more websites, and more websites means more vulnerabilities.
One such case is Sri Chaitanya's ePraghna.
A friend of mine was enrolled at Sri Chaitanya Institute for his JEE preparation. In spite of being a fairly popular institute in South India, producing toppers since time immemorial, and claiming to have "taught" more than 7,50,000 students, its online presence security, unfortunately, falls way shorter.
Strike One!
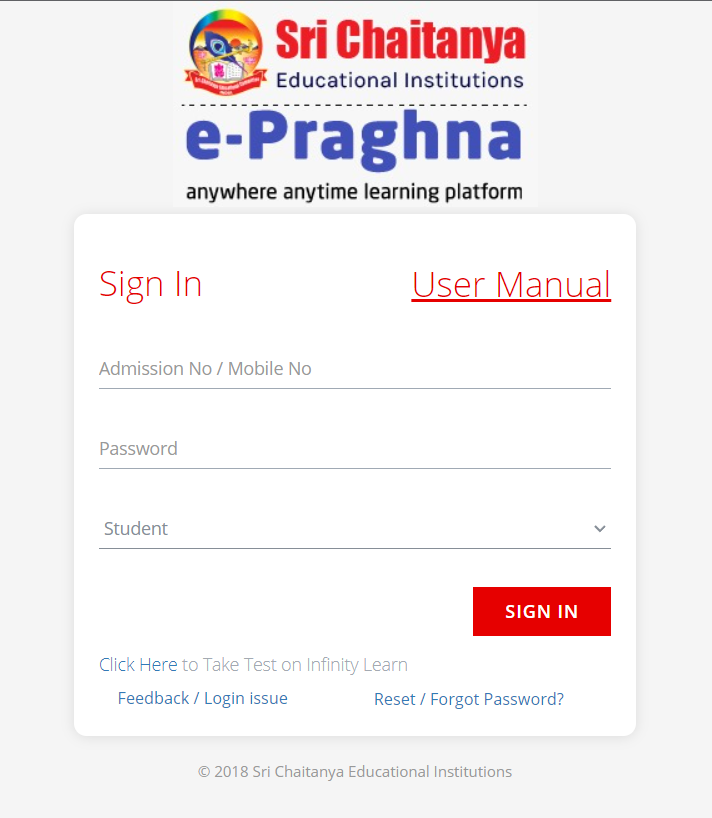
Upon login, the website presents a very innocent looking login page. At the time, I did not have the correct password to my friend's account as he had changed it recently, so I began to look at the 'Forgot Password' section of the page.
Although I was not very adept at browser traffic sniffing, I noticed something very unusual, which was that the mobile number check prompt was pretty fast, and it seemed like no server sided validation was taking place to validate the phone number.
This was step one. I fired up burpsuite and found that the mobile number was returned in full and in plaintext, and validated client side, on the GET call to:
https://www.epraghna.com/forgotPassword?admNoVal={admissionNumber}
Thus, a vulnerability that could be (hypothetically, of course) used to scrape the phone numbers of everyone registered to the institute.
Strike Two!
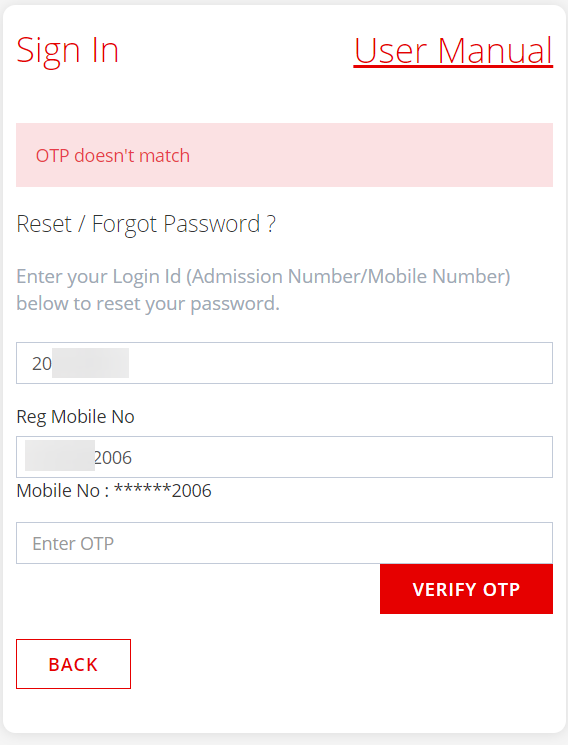
After bypassing the first check, there lay the problem of validating the actual OTP, but I found out that it could be controlled client side as well.
The OTP request call was a GET call to:
https://www.epraghna.com/getForgotSmsOtp?phoneNo={arbitraryPhoneNumber}
No association of the OTP with the student account whatsoever, which is utterly absurd and doesn't even make sense.
Thus, a vulnerability that could be (hypothetically, of course) used to spam OTPs to arbitrary phone numbers, essentially becoming an SMS bomber.
Game Over!
There exists a third GET call to:
https://www.epraghna.com/checkforgotSmsOtp?phoneNo={phoneNumber}&otpVal={otp}
which seems as if it is validating the OTP in some way, which, yes, it actually is, but looking closely at the JS, it serves no purpose. The check could simply be skipped over, either by some console fuckery, or replicating the subsequent, or the MAIN attack vector of this post.
https://www.epraghna.com/changeStudentPassword?newPasswordVal={newPassword}&stuPassword={newPassword}&admNoVal={admissionNumber}&mobileNoVal={mobileNumber}&otp={otp}
Yes, arbitrary values work and have no association with the student account.
Thus, a vulnerability that could be (hypothetically, of course) used to abuse student auth for malicious purposes!